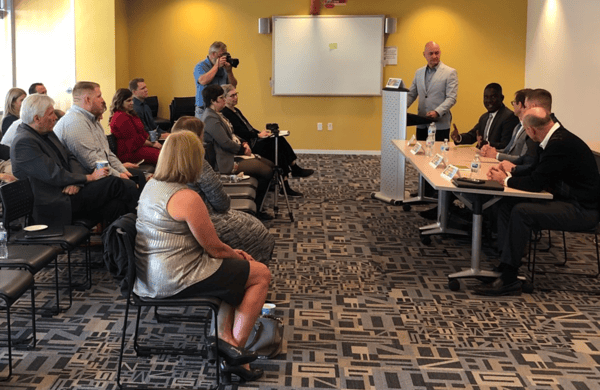
Arizona businesses face evolving privacy laws, enforcement practices and cyber crimes. That’s why the Phoenix Business Journal invited some of Arizona’s leading cybersecurity and legal experts to discuss the cyber problems facing Arizona’s businesses and offer solutions at the Cybersecurity Forum earlier this week. The University of Advancing Technology has been teaching cybersecurity for more than 20 years, which is why the PBJ team invited UAT Provost Dr. Dave Bolman to moderate the panel discussion for the second year in a row.
Privacy and consumer protection laws continue to change and so do enforcement practices. So far, the Arizona Attorney General hasn’t prosecuted a single information breach, but that does not mean he won’t in the future. Many companies don’t realize that hackers aren’t just after their customer data. Cyber criminals also pursue intellectual property information. “Think about how much of your organization’s competitive information shows up in your emails,” Dave told the audience.
New technology is exposing new industries to cyber threats. For example, agriculture is more connected than ever. But how many Arizona farmers are thinking about cybersecurity? With the advent of new information security technology and products, the landscape of liability is also changing. Arizona small business owners should consult legal experts like Osborn Maledon’s William Furnish to better understand who is truly responsible when a breach occurs.
Business owners should also consider looking into cyber risk insurance, which is becoming a big business. But people need to know how to ask what’s covered and what’s not. It’s always a good idea to consult a cybersecurity lawyer.
Cyber criminals are also finding new ways to exploit small businesses to reach bigger targets. For example, hackers responsible for the massive Target breach broke in through a small HVAC company that contracted with the mega retailer. Moving forward, companies of all sizes should consider vendor risk management.
Risk is not black and white; it’s a spectrum. Businesses must decide how much risk they are willing to take on, but it’s easy to handicap your business if the mindset is “No trust, no risk.” Arizona businesses can consult the experts at Terra Verde to determine what works best for them and learn how to create value from security and compliance investments.
The first step in protecting your organization is knowing what data you want to protect and then evaluating all the places where that information is stored. Dump any data you don’t need. “Clean your own house first,” Dave said. The next step is making sure all of your vendors and business partners are on the same page.
Are you ready to secure your business? Reach out to Terra Verde Sr. Security Manager Jacques Lucas to start the conversation.
Want to learn how to fight cyber crime and protect people’s data? Check out Arizona's first NSA-Certified Center of Academic Excellence cybersecurity degree program at the University of Advancing Technology.





Comment